The worst is not always certain… but how do you react when the last ramparts give way, and ransomware has destroyed all your backup files?
The ransomware threat is regularly breaking new ground: groups are no longer content with encrypting data, but are also methodically attacking backup devices – the ultimate protection against a complete IT system paralysis.
This article is the story of an advanced technical intervention, which takes us behind the scenes of a digital rescue usually considered complex to achieve…
Or how our team was able to recover all the data of an architecture firm, after a ransomware attack that had meticulously destroyed any fallback solution?
This case study documents the complete recovery process that enabled us to restore 580 GB of business data (411,000 files in 79,417 folders) from media considered irretrievably compromised.
Compromised infrastructure: the impact of a targeted attack on a professional storage system
A Colombian architecture firm recently contacted us following a cyber attack of uncommon intensity… Unlike more conventional attacks where data is simply encrypted, the attackers had opted for a particularly destructive strategy:
- Complete reset of RAID disks
- Formatting of the external USB backup disk (USB COPY)
- Deliberate compromise of Hyper Backup file integrity.
This aggressive approach was aimed ateliminating any possibility of recovery without ransom payment, illustrating a worrying trend where cybercriminals are now deliberately targeting data protection mechanisms, with complete control over the computer system.
Insufficient standard solutions
Before calling on our services, our customer had already gone through a whole series of conventional solutions.
Attempts with consumer software such as PhotoRec had yielded only partial and unusable results.
Escalation to Synology technical support, all the way to the top of the organization, had ended in an admission of powerlessness in the face of the severity of the damage. Even consultation with several local IT specialists failed to resolve the situation.
Despite this major mobilization of resources and skills, no viable solution emerged.
This was a particularly complex case, which went beyond standard recovery procedures, and required specialist skills in post-cyber-attack data recovery.
In-depth technical analysis
Our team received two items for analysis:
- An image of the 1 TB external disk containing the Hyper Backup backups
- One of the 4TB RAID1 disks formatted in BTRFS.
Initial examination revealed several major technical challenges:
Challenges related to the BTRFS file system
The BTRFS system, although robust and high-performance, has an architecture that makes it considerably more difficult to recover data in the event of corruption. Its structure, which separates metadata (file names, tree structure, attributes) from the data itself, can lead to a situation where files are recoverable, but without their organization or identifiers.
The complexity of the Hyper Backup format
Hyper Backup’s proprietary format, with its .bucket, .index, .bkpi and .hbk files, represents an additional layer of complexity. The backup also used advanced features such as compression, making access to data even trickier in the event of corruption.
Dual recovery methodology
To deal with this situation, our team adopted a two-stage approach:
1. Extraction from the RAID disk
Our first analysis focused on the 4TB disk configured in RAID1 with a BTRFS file system. We were able to extract files, which was good news in itself. However, we quickly identified a major limitation: file names and directory structure were lost.
This is typical of BTRFS recoveries after major corruption. This modern file system uses a fundamentally different approach to traditional systems, separating metadata (names, paths, dates, etc.) from the data itself. When metadata is corrupted, it is often possible to recover the raw data, but without its essential attributes.
Although technically successful, this approach would have required considerable time to reorganize and identify the files. For an architect needing rapid access to specific projects, this solution was not optimal.
2. Rebuilding Hyper Backups
Our second approach focused on the external backup disk. Analysis revealed around 580 GB of data in the form of proprietary Hyper Backup, .bucket and .index files.
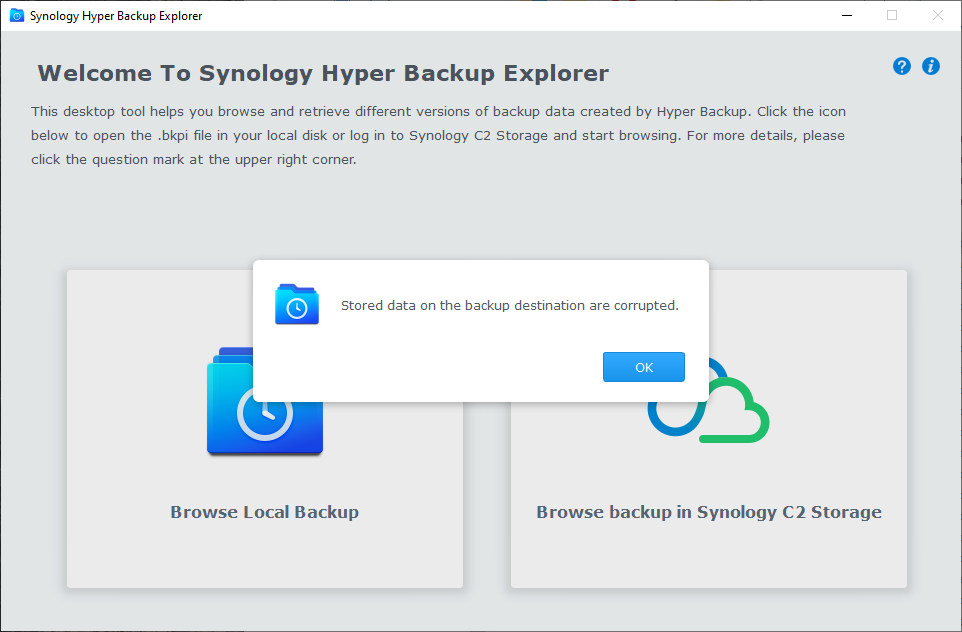
But the official Synology Hyper Backup Explorer utility encountered recurring error messages such as “The data stored in the backup destination is corrupted.”
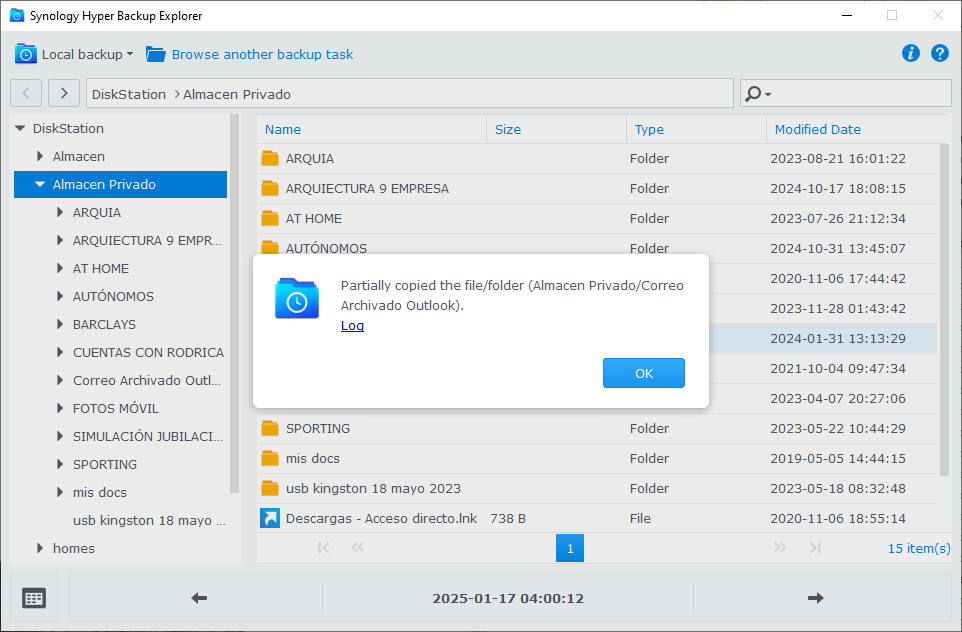
or “File/folder partially copied or restored”.
This tool only managed to recover around 75 GB of data (i.e. 15% of the total) before encountering blocking errors.
Development of proprietary solutions
To get around this type of impasse, our engineering team implemented a solution developed in-house: our Synology Backup Extractor tool. This proprietary tool has been specially designed to deal with situations where official tools fail due to partial corruption of Hyper Backup backups.
Technical analysis of the situation revealed several specific challenges:
- Compression enabled: the backup used compression, a feature that optimizes disk space but significantly complicates recovery in the event of corruption.
- Corrupted .bucket and .index files: these files form the architecture of the Hyper Backup, and their corruption compromises access to the underlying data.
- Partial access with Hyper Backup Explorer: the official tool managed to recover around 75 GB of the 500 GB present, but regularly stopped with errors, displaying the message “Partially copied the file/folder”.
Our approach was to reconstruct the file and folder address mappings to bypass the corrupted metadata sections. This highly technical method required an in-depth understanding of the internal structure of Hyper Backup’s backup format, the fruit of our expertise in recovering data from NAS environments and more specifically from a Synology NAS.
The results
The intervention achieved particularly satisfactory results:
- Recovery of all 580 GB of business data
- Restoration of 411,000 files organized in over 79,000 folders
- Complete hierarchical structure preserved
- Preservation of original file names and attributes
For this architectural firm, the difference was vital: access to all their professional projects (plans, 3D renderings, contractual documentation) represented the safeguarding of several years’ work, as well as the continuity of their business.
Lessons learned and strategic recommendations
This intervention has enabled us to formulate several essential recommendations for the protection of professional data:
Advanced protection of backup devices
Cybercriminals now consider backup systems to be priority targets. It is therefore essential to take the following measures:
- physically disconnected backups (air gap)
- Read-only media
- Reinforced authentication for access to backup systems
- Scheduled back-up integrity checks
Application of the 3-2-1 strategy
This situation perfectly illustrates the relevance of the 3-2-1 rule:
- 3 independent copies of your data
- On 2 different types of media
- Including 1 copy stored off-site
In our customer’s case, the external backup was connected to the main system, making it vulnerable to the same attack – a common configuration that can be exploited by hackers.
The importance of specialized solutions
This intervention demonstrates the need for highly specialized recovery tools in the face of modern attacks. Consumer software and even manufacturers’ official tools show their limitations in complex situations involving :
- Advanced file systems (BTRFS, ZFS, ReFS)
- proprietary backup formats
- Intentional corruption by malware
Critical expertise in the face of evolving threats
The growing sophistication of cyber-attacks, now specifically targeting backup mechanisms, makes an expert approach to data recovery essential.
This ransomware data recovery case demonstrates that even in situations that conventional tools consider irrecoverable, solutions exist thanks to advanced technologies and specialized data recovery expertise.
For businesses and professionals using Synology NAS or other advanced storage solutions, this feedback underlines the importance not only of a robust data protection strategy, but also of having identified partners with the technical capabilities to intervene in the event of a major disaster.
Need help with your Synology NAS?
If you encounter a similar situation with a compromised Synology NAS or corrupted backups, our team of ransomware data recovery experts is available to assess your situation.
Our emergency response team is available 24/7 for critical situations requiring immediate intervention.
We’re on hand to resolve even the most complex ransomware attacks.





